By Anya Sastry
Introduction
For decades now, statecraft and the methods through which nations strategically interact with each other have developed alongside the emergence of new technologies and tools. More specifically, we have seen a broadening of governmental and military strategy through the emergence of cyber space and the various facets of that realm. Due to its fairly new existence, many states are still navigating the boundaries of this cyber space and thus present fascinating case studies through which to view the kind of role that cyber tools play in their strategies. Considering the norms surrounding the use of cyber tools and possible actions that states will take with access to these new tools, Mazanec (2015) posits that “In the absence of firmly established norms governing cyber warfare, states may also be exhibiting an abundance of caution as they slowly test the limits of what the international community deems acceptable behavior in cyberspace.” With regards to the uncertainties of this new space, Mussington (2019) asserts that “This ambiguity…has been voraciously exploited by an assortment of state, non-state and suspected proxy actors…The result has been a near constant drizzle of activity in cyberspace calculated to fall into a ‘grey zone’.” I argue that in this new iteration of warfare, where complex cyber tools are readily available for use, there is an increased potential for governments to abuse their cyber power in their desire to establish dominance over another state or group.
The Israeli use of cyber tools in its military occupation of the Palestinian Territories presents a clear depiction of this. From Blue Wolf to Pegasus spyware to Facebook censorship, there are many invasive cyber experiences that Palestinians must face in the military occupation. Through a myriad of cyber tools, cyber strategy is now a significant facet of the daily operations that the Israeli government and military carry out. Through interviews, academic reports, news articles, first-hand testimonies, and visual evidence, I arrive at the following conclusion: through the significant use of cyber tools, such as surveillance technology, hacking software, and social media algorithmic censorship, the Israeli government and military perpetuate their current-day occupation of the Palestinian Territories by taking advantage of a poorly structured governmental system and actively creating an environment that disregards basic rights to privacy and suppresses the Palestinian voice.
Structure of Israeli Military Cyber System
Within the governmental system, cyber policy is driven first and foremost by the Israeli National Cyber Directorate, also known as the INCD. This cybersecurity organ, as one of the main bodies within Israel’s cyber system, maintains a myriad of responsibilities and tasks. INCD not only deals with cyber policy and operational implementation, but also works in coordination with other existing governmental and military groups, such as Mossad, Israel Defense Forces (IDF), Ministry of Justice, Israeli Police, and Shin Bet. The core issue with the INCD, however, especially when taking into account the considerable reach this organ has within Israel’s cyber system, is the centralization of its power and capabilities into the Office of the Prime Minister (see Fig. 1). The “Cybersecurity and the National Cyber Directorate” bill, which was introduced in 2018 and was later reintroduced with revisions in 2021, provides a legal framework for the INCD that many have deemed problematic due to how it allows the Prime Minister complete access to the INCD as a cyber tool without any oversight or system of checks and balances.
One such critique was on the lack of sufficient transparency and as the Library of Congress reports, “According to the IIA, the Memorandum is conspicuously lacking in transparency mechanisms, as well as parliamentary and public oversight of its activities. According to the proposed bill, the INCD’s activity focuses on the relationship between the prime minister, the INCD’s director, the privacy supervisor and the Supervisory Committee. There is no reporting to the Knesset or to the general public. The duty of extreme secrecy that is imposed on INCD’s employees and on the Supervisory Committee…prevents the publication of any information to the public” (Library of Congress). This centralization of power and complete lack of oversight for one of the major bodies within the cyber system impart the Israeli government with the capabilities to order cyber operations that are potential human rights violations and fundamental obstructions of democratic values.
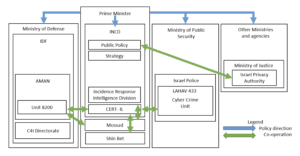
Fig. 1. Frei, Jasper, “Oversight Diagram,” 2020.
Cyber Surveillance, Hacking Operations, and Social Media Censorship
I identified three main cyber tools through which the Israeli government and military maintains their military occupation and subordination of the Palestinian Territories. The first is the Blue Wolf technology that is being used by Unit 8200 within the Israeli military on Palestinians in the West Bank and specifically, Hebron. Through this technology, which is programmed into a provided phone, soldiers can take photos of an individual and run it through a database filled with thousands of stored photos, as well as highly private information, in order to identify the individual before them. Different colors pop up on the app depending on whether this individual has been assigned an arrest, detain, or release order.
Over Zoom, Cathrine Abuamsha from 7amleh (the Arab Center for Social Media Advancement) provided additional information on Blue Wolf, stating that “[Blue Wolf] is connected to a very wide biometric data bank or database…they take pictures that connect with our faces or with our ID numbers…if they take a picture that is connected to this Blue Wolf and it shows that, for example, I am a threat to the army or to the state of Israel based on my opinions and my expressions or whatever activism I do, they will stop you or they could detain you or they could do whatever they do. So, imagine, this is a violation of privacy, a violation of your freedom of opinion and expression, also your dignity. All your information is exposed and your face is exposed and you are basically not controlling any of your movement” (Abuamsha). Several testimonies published by The Guardian from former Unit 8200 soldiers also speak to the focused intelligence that the IDF gathers on Palestinians, regardless of whether they are involved in violent acts or not, in order to further pointed political agendas and suppress Palestinians.
The second tool is the highly controversial Pegasus spyware. In 2021, the Israeli government utilized the Pegasus spyware created by the NSO Group to hack into the personal cellular devices of leaders of various Palestinian human rights groups and NGOs. These prominent and internationally-renowned groups include Al-Haq Rights Group, Bisan Center for Research and Development, and Addameer Prisoner Support and Human Rights Association. A technical investigation run by Frontline Defenders and confirmed by Citizen Lab and Amnesty International discovered this hacking operation and released its findings for the public. Much of the time I spent with Cathrine was dedicated to discussing the Pegasus hacking. She described the spyware as a zero-click hacking operation, meaning that the user of the device does not have to click anything in order for the spyware to infect the device. Once Pegasus is installed, the device becomes a “portable surveillance tool by gaining access to the phone’s camera, microphone, and text messages, enabling surveillance of the person targeted and their contacts” (“Spyware Used to Hack”). The Pegasus spyware, the same technology used to surveille French President Emmanuel Macron, is dangerous and invasive to the point where many countries around the world have blacklisted it. Despite these international standards, the Israeli government continues to utilize it on Palestinians. Following the condemnation of the Israeli government for utilizing NSO’s spyware in such a manner, the government made the decision to designate the human rights groups of those who were hacked as terrorist organizations based on secret evidence, as well as indefinitely detained without reason one of the individuals whose phone was hacked.
Finally, through partnerships with the private sector, the Israeli government also utilizes social media censorship to further its occupation of the Palestinian Territories. The Israeli government maintains a strong relationship with Meta, the owner of apps such as Facebook and Instagram, two apps that are widely used among Palestinians. While in Jerusalem, I met with a Palestinian by the name of Ahmad Barakat who explained the intricacies of this relationship. Ahmad engages in digital advocacy work related to his past and ongoing experiences with the Israeli government and Meta. He began our conversation by sharing that in 2016, the Ministry of Affairs of Israel met with Meta regarding Palestinian content. Following this meeting, Palestinians began to experience significant censorship on Facebook and Instagram, whether it was through content removals, account restrictions, or shadow-banning, leading many to believe that the Israeli government tasked Meta with altering their algorithms to censor Palestinians (see figures below). Ahmad took it upon himself to test his theory and he related his findings, stating that “I try to test by myself, to write several words in Arabic about something related to Palestine and to the cause of Palestine, to terrorism and everything, okay? And I did the same thing with the Hebrew language…I got my account closed because of the Arabic content…there is two standards for the content related to Arabs or to Jewish…When you see the Israeli pages, you will see that, for example, Death to Arabs, Kill Arabs…no one tell them anything” (Barakat).
Additionally, Ahmad discussed the shadow-banning that many influencers, both in the Middle East and abroad, experience when posting advocacy-related content regarding Palestine, saying that reach goes down by as little as fifty percent. Many creators and influencers who post about Palestine fail to show up in search results until their full usernames are typed into the search function of Instagram. Furthermore, they are barred from going live on their accounts (see Fig. 2).

Fig. 2. @shaymaalshiri and @snake for @muslim on Instagram, “This Is What Social Media Censorship Of Palestine Looks Like,” 2021.
He also mentioned restrictions on specific words, sharing that “We have started seeing the new restrictions from the content for some words like, for example, shaheed. Shaheed in English is martyr…when someone is killed from Palestine, we call him shaheed…on Facebook, you can’t write this” (Barakat). One of Ahmad’s clients is a Fatah-centered student group at Birzeit University in the West Bank. Referring to his work with the group, Ahmad said “…I worked with them as a consultant…Before, about two months, they published some photos from their activities in university and one of the photos contained name of [group similar to Hamas]. It contained only the words. They give them a warning message that they will close the account, just because of some words inside a picture for a students activity” (Barakat). Ahmad, having posted about the activities himself, faced account restrictions himself after he posted about these student activities and referred to former Palestine Liberation Organization (PLO) chairman, Yasser Arafat, as a shaheed or “martyr” (see Figs. 3 and 4).
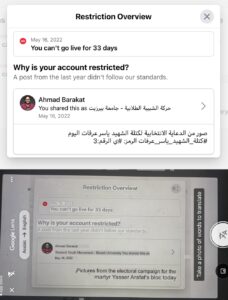
Fig. 3. Ahmad Barakat, “Screenshot of Account Restrictions & Translation,” 2022.
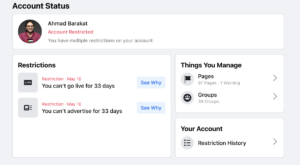
Fig. 4. Ahmad Barakat, “Screenshot 2 of Account Restrictions,” 2022.
Recommendations
I have found that a complete lack of oversight and accountability allows for the exploitation of cyber tools, such as surveillance technology, spyware, and media algorithms, for the purpose of maintaining the occupation of the Palestinian Territories. In this new and emerging space of cyber warfare, the Israeli government and military have taken complete advantage of poorly-constructed legal frameworks and norms in order to further their own power ambitions. The first and most important step to combating such actions is to rework the legislative framework upon which the INCD is built. Decentralize the responsibilities within this organ and incorporate a system of checks and balances so that full power is not placed in the hands of one individual with a political agenda. Implement a system that factors in consequences and methods of accountability, a system that demands Unit 8200 to think twice before maintaining total and invasive surveillance of Palestinians. If this foundational component is not fixed, the Israeli government and corresponding military intelligence units will continue to exploit their access to powerful cyber tools and partnerships in the greater plan of occupying the Palestinian Territories.
Bibliography
Abuamsha, Cathrine. Personal Interview. 20 June 2022
Anonymous. “Testimonies from people who worked in the Israeli Intelligence Corps.” The Guardian, September 2014. https://www.theguardian.com/world/2014/sep/12/israeli-intelligence-unit-testimonies. Accessed 7 July 2022.
Barakat, Ahmad. Personal Interview. 8 June 2022.
Barakat, Ahmad. “Screenshot of Account Restrictions & Translation.” LinkedIn Messaging, 12 July, 2022.
Barakat, Ahmad. “Screenshot 2 of Account Restrictions.” LinkedIn Messaging, 12 July, 2022.
“Spyware Used to Hack Palestinian Rights Defenders.” Human Rights Watch, 8 November 2021, https://www.hrw.org/news/2021/11/08/spyware-used-hack-palestinian-rights-defenders. Accessed 7 July 2022.
“Israel: Knesset Passes Amendment Law Recognizing Role of National Cyber Directorate in Protecting Cyberspace.” Loc.gov, Library of Congress, 22 July 2019, https://www.loc.gov/item/global-legal-monitor/2019-07-22/israel-knesset-passes-amendment-law-recognizing-role-of-national-cyber-directorate-in-protecting-cyberspace/.
Forty-three Veterans and Reservists of Unit 8200. “Open Letter to Prime Minister Netanyahu.” Received by Prime Minister Mr. Benjamin Netanyahu, Institute for Palestine Studies, 12 Sept. 2014, https://www.palestine-studies.org/en/node/188335. Accessed 7 July 2022.
Frei, Jasper. Israel’s National Cybersecurity and Cyberdefense Posture. Center for Security Studies at ETH Zürich, 2020, pp. 12-15, https://css.ethz.ch/content/dam/ethz/special-interest/gess/cis/center-for-securities-studies/pdfs/Cyber-Reports-2020-09-Israel.pdf. Accessed 7 July 2022.
Mazanec, Brian M. “Predicting Norm Evolution for Cyber Warfare.” The Evolution of Cyber War, pp. 163, https://www.jstor.org/stable/j.ctt1d989jr.12.
Mussington, David. “Strategic Stability, Cyber Operations and International Security.” Governing Cyberspace during a Crisis in Trust, Centre for International Governance, 2019, pp. 58, https://www.jstor.org/stable/resrep26129.13.
@shaymaalshiri, @snake. “This Is What Social Media Censorship Of Palestine Looks Like.” @muslim on Instagram, 14 May, 2021, https://www.instagram.com/p/CO4Nv5pDLVH/.